Leaky Meow Mac OS
Some of you will love this, and some of you are going to flame me. I don’t care about the haters though. Even though a fellow TYPO3 developer friend pointed out regarding my solution, “There has to be a better way. There probably is”, I’m posting this as a help to all the Firefox users of the world who are sick to death of the phantom Firefox memory leaks.
Given that MacOS is currently on version 10.15.3, the code could suggest Apple is working on support for a broad array of AMD processors sooner rather than later. It also adds to previous leaks.
- If you have a Mac with an M1 chip, you can run iPhone and iPad apps and games right on your Mac. Apple has been steadily adding more capabilities to this feature, but the latest MacOS 11.3 update.
- The Diagnostics section varies depending on the age of your Mac and OS: on older systems (where the diagnostics page has a blue background) you'll need to select the middle tab, Hardware Tests.
Then build it and run to test how the memory leak is detected: admins-Mac:test2 admin$ clang -fsanitize=address -g mleak.c; ASANOPTIONS=detectleaks=1./a.out 556AddressSanitizer: detectleaks is not supported on this platform. Abort trap: 6 admins-Mac:test2 admin$ How I can detect the leak? I need to use it for my large application. AirPods Support. Forgot Apple ID or password. Billing and subscriptions. Trade in with Apple. Turn an eligible device into credit towards a new one, or recycle it for free. Apple Trade In is good for you and the planet.
We all know Firefox leaks memory for one reason or another. It’s been years. Plugins have come and gone and Firefox just leaks all the time. Period. What to do?
It’s time to hit Firefox with a sledgehammer. Like a boss.
This requires just the slightest bit of Mac OS savvy, but not much, or else I couldn’t have done it. Windows is a bit easier, but I’ll post the Mac version first and follow up next week with the Windows solution.
The solution is to simply kill and restart Firefox as quickly as possible. Boom. Done. Firefox goes from sappy to snappy in about 1 second. Firefox tries to restore you tabs when it “crashes” so you should be good. On the Mac, you might get the “restore” or “new session” buttons. On the PC, for me at least, it comes right back up without the question.
This has been tested on Firefox 3.x, 4, and now 5 on both Mac and PC. Your mileage may vary.
Make sure you aren’t composing an email in a webmail interface or anything before you test this!
But wait! Am I really sure Firefox has a memory leak? I present my anecdotal evidence:
How to kill and restart Firefox on a Mac in 1 second
- Create a text file, like “killFirefox.txt” somewhere on your Mac.
- After saving it as a .txt file, change it to “killFirefox.command”
- Paste this into it:
- Now open Terminal and navigate to wherever you saved the file. You’ll have to Google how to use Terminal commands, or get an “open terminal here” plugin for Finder (like I have)
- Once you are in the directory where “killFirefox.command” is, run the following command to make your .command file executable. This means that after you do this, you’ll be able to double-click “killFirefox.command” and the script will run:
- Now go back to Finder or wherever you saved the file, and drag it to the RIGHT side of the “dashed line” on your dock if you want one-click access to the process:
- Try it!
- Happy Firefox rebooting! Goodbye slow and sappy Firefox—until a real solution is in place!
You may have to alter the “sleep 1” to something longer, like 2 or 3 seconds if your Mac is too slow. You may also have to put in a different path, but I’m no terminal expert. Also, to set the Terminal window to close after the process finishes, you’ll have to edit the preferences like this: Terminal > Preferences > Settings > When the shell exits = Close the window
How to kill and restart Firefox on a PC in 1 second
- Create a file, like “killfirefox.txt” on your desktop or somewhere handy
- Paste this into it:
- You’ll want to make sure you put in your user account name in the path, and delete the “Your User…” holder text
- Your path to firefox.exe, as listed above, might also be in a different place. You’ll have to find it and confirm.
- Rename the file extension from “.txt” to “.bat”
- Double click your new .bat file and voila!
- Make a shortcut and drag to your quick links bar, or some other handy place
So you have a better way to do this?
Save your negative comments for the comments section on msnbc.com. In the meantime, post instructions on a better way. For example, how to do this in AppleScript so you end up with a real “app” you can put in the Dock in a nice way.
Any other thoughts? Let’s here them!
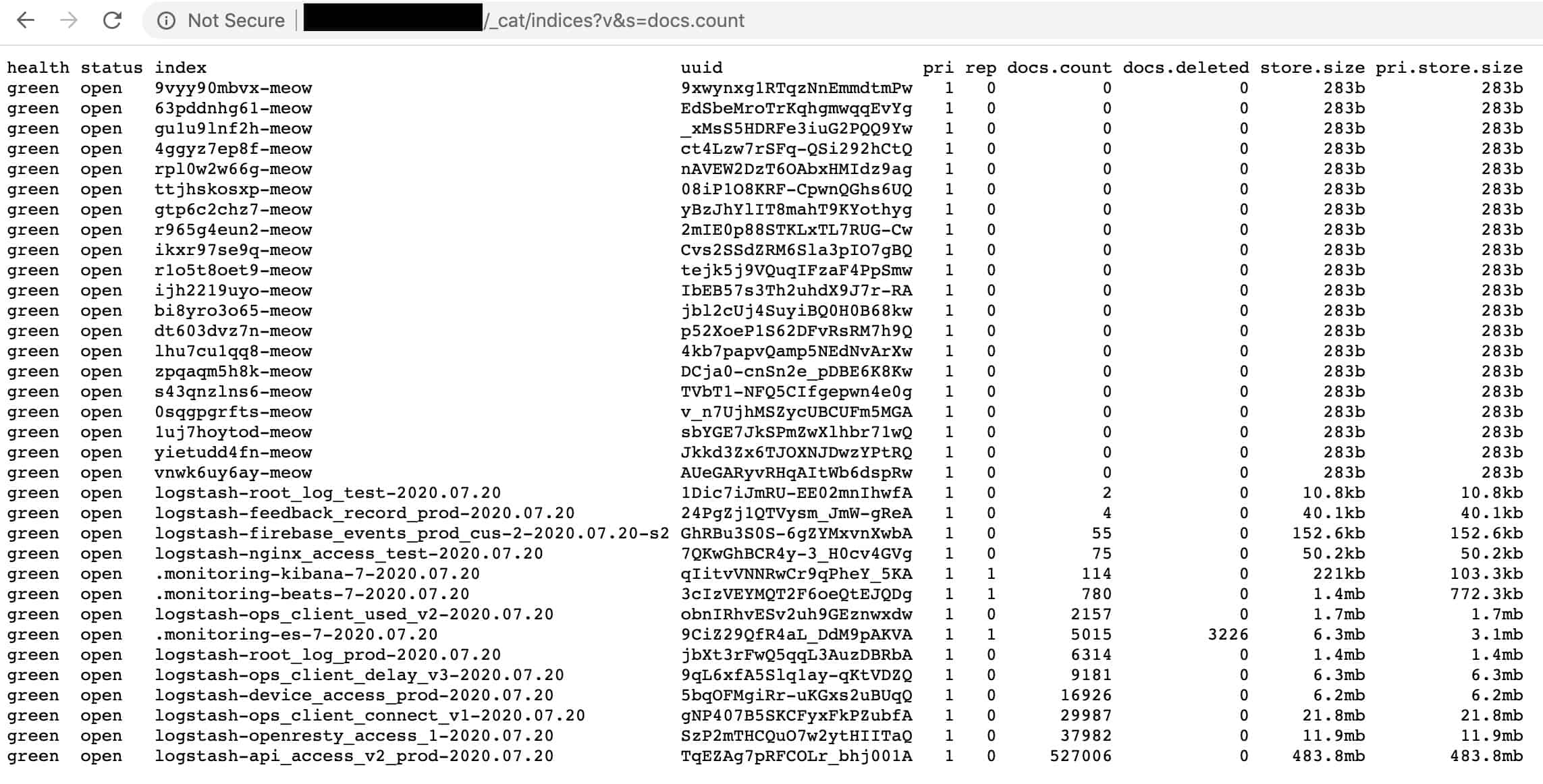
07/25 Update added below. This post was originally published on July 22nd, 2020.
Hundreds of unsecured databases exposed on the public web are the target of an automated 'meow' attack that destroys data without any explanation.
The activity started recently by hitting Elasticsearch and MongoDB instances without leaving any explanation, or even a ransom note. Attacks then expanded to other database types and to file systems open on the web.
A quick search by BleepingComputer on the IoT search engine Shodan initially found dozens of databases that have been affected by this attack. Recently, the number of wiped databases increased to over 1,800.
These attacks have pushed researchers into a race to find the exposed databases and report them responsibly before they become 'meowed.'
Cat's out of the bag
One of the first publicly known examples of a Meow attack is an Elasticsearch database belonging to a VPN provider that claimed not to keep any logs.
Discovered by researcher Bob Diachenko, the database was initially secured in July only to become exposed again five days later.
The second time, though, the owner no longer received a well-intended notification. Instead, they got ‘meowed,’ with almost all records getting wiped.
Diachenko told BleepingComputer that there are not many details about the attacker or the purpose of their actions. He says that the attack appears to be an automated script that “overwrites or destroys the data completely.”
Researchers first observed the ‘meow’ database attacks at the beginning of the week. They could be the work of a vigilante trying to give administrators a hard lesson in security by raining destruction on unsecured data.
Victor Gevers, the chairman of the non-profit GDI Foundation, saw this type of attack, too. He says that the actor is also attacking exposed MongoDB databases, hitting as much as they can.
He also saw the first ‘meow’ attacks a few days ago, with a recent one occurring on July 22, just a couple of hours after a GDI volunteer disclosed it responsibly to the owner.
Mac Os Download
The researcher observed on Thursday that whoever is behind the 'meow' attack is apparently targeting any database that is insecure and reachable over the internet.
He saw these attacks.
07/25 Update: The Meow attacks continue to escalate with almost 4,000 databases deleted as of Saturday, July 25th.
A new search on Saturday using Shodan shows that more than 3,800 databases have entry names matching the 'meow' attack. More than 97% of them are Elastic and MongoDB.
While it is still not known why the threat actors are wiping databases, a security researcher named Anthr@X discovered that the attacks are being conducted via ProtonVPN IP addresses.
Obstructing researchers
If behind these incidents are positive intentions, sometimes nothing good comes out of them and valuable data that could be lost in the process.
Data leaks from unsecured MongoDB and Elasticsearch instances reachable over the public internet are on a descending curve, but there is still some “very sensitive” information exposed.
As Gevers puts it, “some leaks bring bad things to the light, which need to be shared,” and wiping them brings benefits to no one.
“It is becoming a race to find these leaks as early as possible. This reduces the amount of time that can be spent on researching and reporting” - Victor Gevers
Whoever is behind the 'meow' attacks is likely to keep on targeting unsecured databases, aggressively destroying them. Administrators should make sure that they expose only what needs to be exposed and make sure the assets are properly secured.
Leaky Meow Mac Os 11
Update [July 25, 2020]: Added image with overall status of 'meow' attacks from LeakIX. Recalculated amount of deleted databases due to Meow attacks.